- • Ransomware attacks surged in December 2025, with a 58% year-over-year increase in observed victims.
- • Mid-tier groups like Qilin and Akira have increased their operations.
- • Increase in BYOVD attacks and the use of new toolkits like PowerTool and Killer Ultra, lowering the barrier to entry for attackers.
- • AI tools are used to determine ransom amounts, create visually alarming ransom notes
Above: Illustration by igorstarr996/DepositPhotos.
BitDepth 1548 for February 02, 2026
The summary sentence of the GRIT Ransomware and CyberThreat report for 2026 is instructive: “Progress against ransomware and cybercrime remains consistently visible, albeit slow and largely reactive in nature.”
The GuidePoint Research and Intelligence Team has been assessing ransomware threats since 2022, using information from publicly available resources, including statements by threat groups. Alleged victims do not confirm its findings.
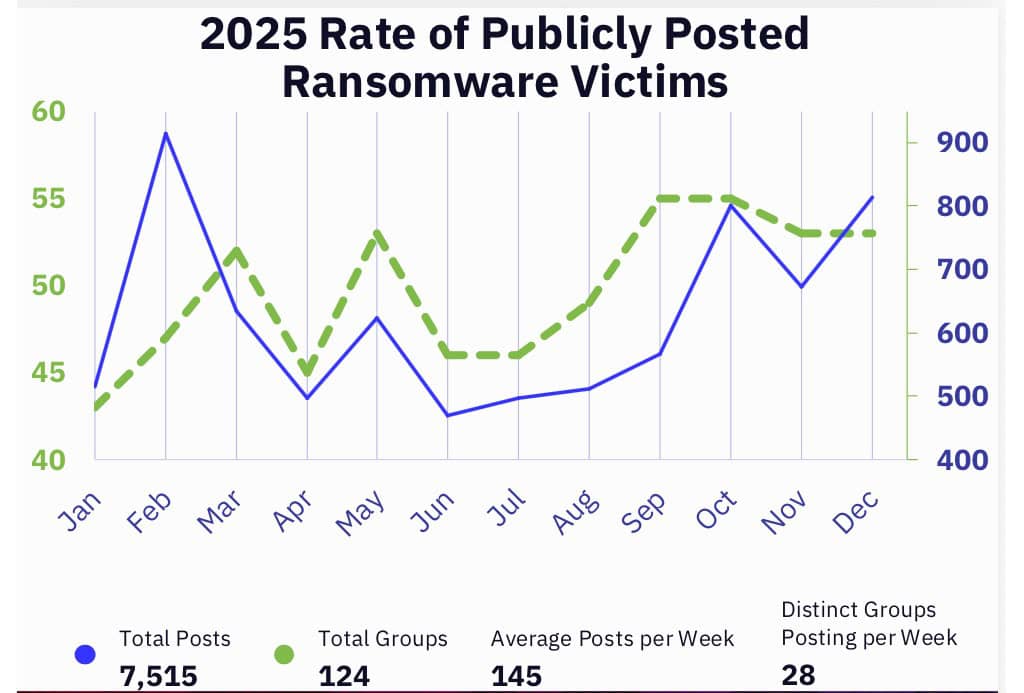
Attacks during the year trended low through the second and third quarter, according to the report, before surging in December to register a 58% year-over-year increase in observed ransomware victims, claimed across 124 distinct and named groups.
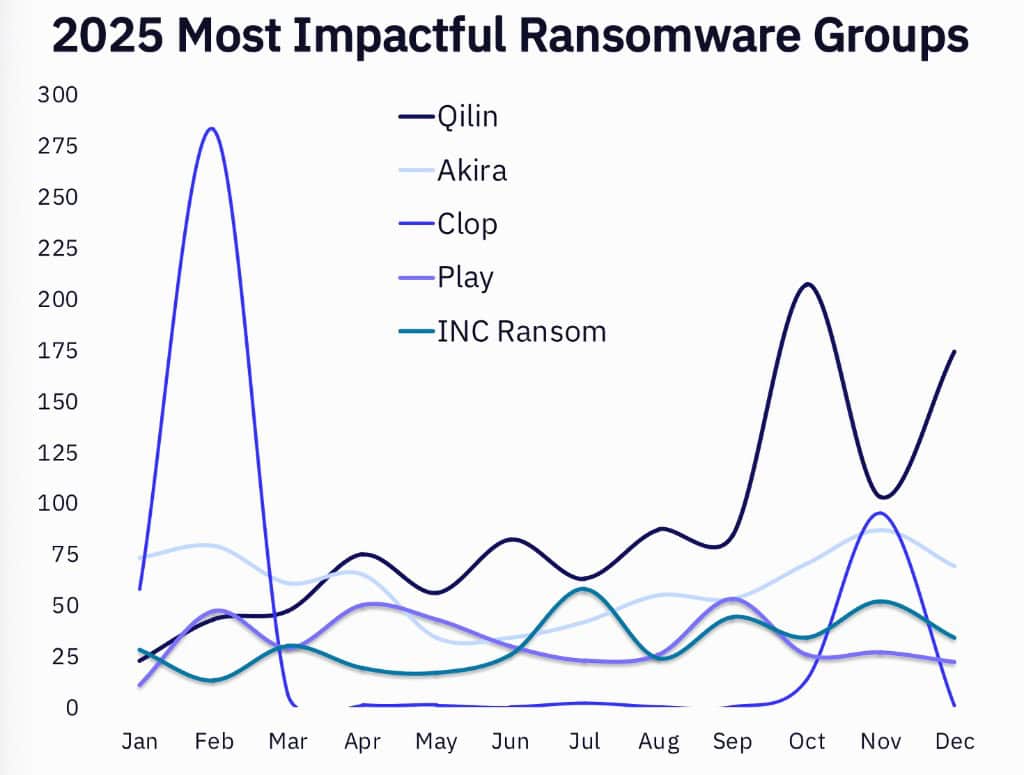
Formerly mid-tier groups, notably Qilin and Akira have stepped up their operations after law enforcement efforts disrupted attacks by LockBit and Alphv.
GuidePoint analysts suggest that these players have absorbed affiliates left behind after law enforcement operations against LockBit and allegations of chaos in the RansomHub operation.
An early surge in 2025 reporting was attributed to the data extortion group Clop, which launched a massive campaign in 2024 but posted its victim lists in early 2025.
The count of victims reported by ransomware groups during 2025 is daunting. GuidePoint counted 7,515 victims, which it gathered from the postings of 124 ransomware groups.
Ransomware attacks follow an ability to pay profile. The manufacturing industry accounted for the largest share of victim organisations, 1060, or 14% overall. Technology, Retail and Wholesale and Healthcare businesses and organisations rounded out the majority profile.
Businesses in the US accounted for 74% of attacks, which mirrors the general profile of attack vectors, which overwhelmingly target US companies. The US was targeted for 55% of reported victims.
The report noted a significant increase in attacks on law firms and attorney’s offices, more than doubling from 196 in 2024 to 455 in 2025.
These attacks may be targeting the sensitive data held by law firms as well as the promise of cybersecurity insurance payouts by businesses likely to have invested in such measures.
What are the attack vectors?
The report notes that ransomware groups targeted “vulnerability exploitation campaigns leveraging zero-day and critical Common Vulnerabilities and Exposures (CVEs) in internet-facing enterprise applications and network perimeter devices.”
These vulnerabilities disproportionately affected Microsoft products in 2025. Key Exploited Vulnerabilities (KEVs) doubled from seven vulnerabilities in the first quarter of 2024 to 16 in the first quarter of 2025.
Fortinet and Cisco were the top targets among infrastructure vendors in 2025. The 2024-2025 surge by Clop targeted Oracle eBusiness Suite, but Bring Your Own Vulnerable Driver attacks have heated up since 2024.
New attack toolkits such as PowerTool and Killer Ultra turned malware that previously required Windows internals expertise into point and click attack vectors, lowering the barrier to entry for ransomware affiliates pursuing these intrusions.
A dark-web site lists 500 legitimate legacy device drivers, trusted but vulnerable, that attackers can exploit.
The report suggests that the drop in attacks in the second and third quarters of 2025 was attributable to the impact of Operation Secure, a law enforcement response that spanned 26 countries that identified and dismantled more than 20,000 malicious IPs and domains that distributed 69 info-stealer variants.
Without this ready source of stolen credentials, a revenue stream for threat actors was temporarily stemmed.
Unfortunately, limiting access to stolen credentials has only meant that ransomware groups have become more creative in how they seek entry points for their destructive payloads.
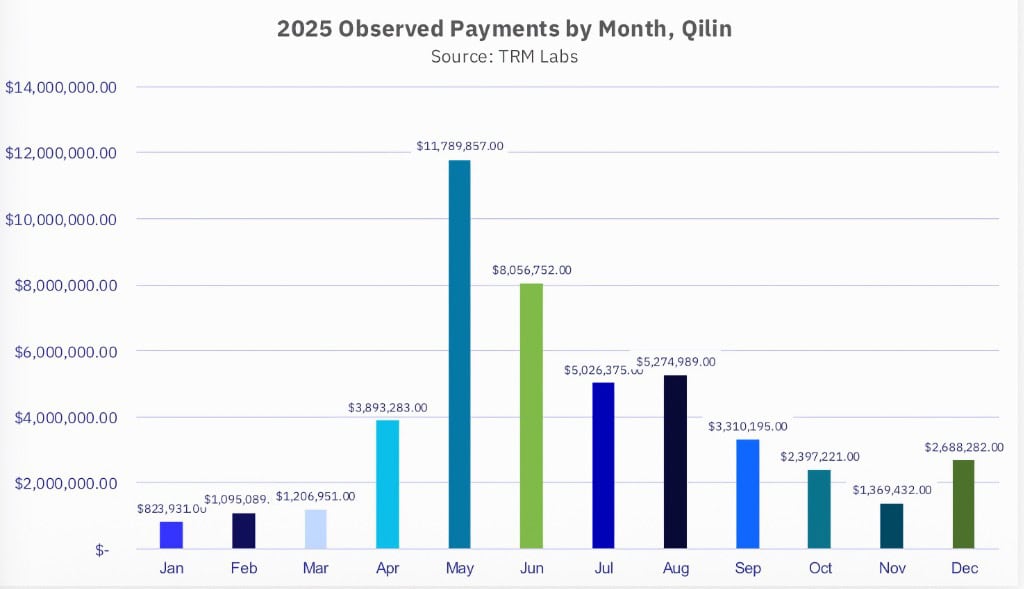
Payment rates have also dropped. While both Qilin and Akira received “outlier payments in the millions,” such windfalls accounted for less than ten percent of observed payments. Average ransomware payments ranged between US$366,000 and $457,000.
Lower payment rates have dropped the average return on investment to between US$47,000 and $90,000 overall and these payments must be shared between affiliate and core group (usually 80/20).
Reduced revenue has not stemmed any enthusiasm for ransomware groups. Qilin extorted at least $47million in cryptocurrency in 2025, with higher ransom demands but lower rates of payments.
Out of 869 posted victims, only 128 made payments. Legislative bans on ransomware payments are still spotty, with the UK introducing its Targeted Ban on payments by public sector organisations.
The International Counter Ransomware Initiative is a non-binding pledge by 48 nations not to make payments, but it is voluntary. North Carolina (2021) and Florida (2022) introduced legislative bans while Australia has mandatory reporting to the government of ransoms paid.
Artificial Intelligence is yet to fully flower as an aspect of these attacks. AI-powered chatbots and AI generated content for language translation and message personalisation improve social engineering tactics and ransomware operators use AI to analyse exfiltrated data to make demands based on financial records and data sensitivity.
Agentic AI is still in its nascent stages, but Anthropic reported in August 2025 that it had quashed an effort to use Claude Code to “vibe code” attacks.
“Claude Code was used to automate reconnaissance, harvesting victims’ credentials, and penetrating networks,” Anthropics noted in a blog post on its findings.
“Claude was allowed to make both tactical and strategic decisions, such as deciding which data to exfiltrate, and how to craft psychologically targeted extortion demands.
Claude analyzed the exfiltrated financial data to determine appropriate ransom amounts, and generated visually alarming ransom notes that were displayed on victim machines.”
Vibe coding using the AI tool was also used to create malware that was sold on the dark web to ransomware affiliates.
This points to an alarming new vector for ransomware in 2026, as more unskilled operators leverage AI tools to level up their gathering of credentials and seek new points of weakness in business defenses.
“The year 2026 will likely see continued convergence of criminal innovation and AI capabilities, demanding that defenders adopt equally sophisticated technologies and intelligence-led approaches,” GuidePoint warned.
“The organizations best positioned to withstand this evolution will be those that prioritize rapid detection and response, implement comprehensive identity and access controls, and integrate AI-powered defenses as essential components of their security architecture rather than experimental additions.”
The GuidePoint report is here.