- Compromised passwords are the root cause of most cybersecurity problems.
- YouTube has the highest password reset frequency with 4.3 times per year.
- The digital identity market is projected to reach USD 133.19 billion by 2030.
Above: Illustration by nao701030455/DepositPhotos
BitDepth#1506 for April 14, 2025
At the heart of most cybersecurity problems is a compromised password.
A password that was guessed.
A password unknowingly shared with a hacker in a phishing operation.
A password found in a data breach that remained unchanged.
It doesn’t matter how well something is locked down if the key can be easily found or replicated.
Passwords are a problem, not least because they are such a pain to think up, to remember and to change with any kind of non-mandated frequency.
Heepsy, an online service for tracking influencers for marketing recently published its findings about password reset frequency.
Why would a user request a password reset? They might have forgotten the password. They might be concerned that a data breach might have left their account vulnerable.
The user might also be in the midst of having their account hijacked through a phishing email and a careless response might make the situation even worse.
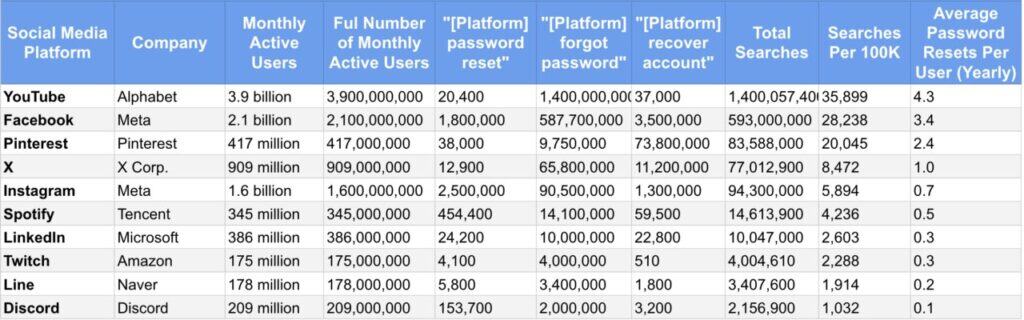
Heepsy tallied the search requests by platform for the terms, “password reset,” “forgot password” and “recover account.”
YouTube topped Heepsy’s evaluation, with 35,899 searches per 100,000 users and an estimated password reset frequency of 4.3 times per year.
The top ten lineup in this ranking of password resets runs the way you would expect. A platform with more users tends to have more password reset requests.
YouTube, with 3.9 billion active users and Facebook with 2.1 billion are ranked first and second, but you have to skip two placings, past Pinterest and X, to get to the third largest platform profiled.
Instagram has 1.6 billion users but just 5,894 search requests per 100,00 users and only 0.7 reset requests per year.
It’s unlikely that Facebook has different levels of user security on Facebook and Instagram, so how and where the platform is used might play a role in understanding the wide variance in password vulnerability.
One key difference between Instagram and the other high volume user platforms, YouTube and Facebook, is access.
Just two per cent of Instagram account holders visit the site on the desktop. It is overwhelmingly a mobile app platform.
The platform with the next largest user base, LinkedIn, with less than a quarter of Instagram’s users at 386 million, logs 0.3 resets annually.
What’s causing this epidemic of password resets and recovery?
Y’all keep using weak passwords. Nordpass noted in its 2024 report on the weakest passwords being used that “123456” again topped the rankings with three million instances found in dark web data dumps.
Following close behind was “123456789” with 1.6 million instances. People. We aren’t even trying here.
Passwords are reused across multiple sites and apps by 85 per cent of users, increasing the ripple effect of hacks.
Weak or stolen passwords are responsible for 80 per cent of data breaches.
Password managers seemed like a good solution at one point. Allow the password manager to create truly gibberish passwords and have just one password that unlocks it.
You can probably figure out what happened next.
With a tempting cache of user passwords available, hackers turned their attention to breaching the security of password manager sites.
Lastpass was attacked twice in 2022, losing source code in the first breach and exposing customer data in the second.
Norton Lifelock warned 6,000 of their customers after being breached in a 2023 credential stuffing attack, a brute force assault that uses passwords sourced in other breaches.
Bitwarden users were lured with a phishing attack in a fake Google ad.
Password State faced a sophisticated attack which began with a fake software update that used phishing techniques to capture user credentials.
Efforts at implementing passwordless systems are still in early implementation. Authenticators tend to be required, not sought out.
Even the best two-factor authentication systems can be annoying to use and the available authenticators from Google and Microsoft aren’t as widely deployed as entry control systems as they should be by now.
It doesn’t help that the lock-in on both systems is so thorough. If you choose to commit to one system, you will have to start the authentication process over entirely to change software.
Google’s authenticator has to do some serious work on feature parity, particularly back-end security and biometric support to match Microsofts’ rival app.
Authenticator apps are the public face of a much larger movement to identity solutions that are embedded in digital services and products.
It’s a growth industry estimated to grow from USD 42.12 billion in 2024 to USD 133.19 billion by 2030.
We won’t be escaping the confusing tyranny of passwords anytime soon, so a personal strategy for creating complex but memorable passwords should be part of your online agenda.