
Above: Illustration by Seamartini/DepositPhotos.
Shiva Bissessar and Javed Samuel of Pinaka Consulting Limited evaluate the blockchain-cryptocurrency payment regime that fuels ransomware payments. Republished with their permission. Pinaka Consulting is an Information Security based consultancy with specialization in digital currency, blockchain and Central Bank Digital Currency (CBDC).
What do the following entities have in common; ANSA McAL, Massy Group, Beacon Insurance, Attorney General’s Office Trinidad and Tobago and Telecommunications Services of Trinidad and Tobago (TSTT)? Since 2020, they’ve all fallen victim to cyber incident which resulted in impact to their service delivery. At least three of these entities have confirmed their incident was ransomware related.
In the January 2023 paper, “An Anatomy Of Crypto-Enabled Cybercrimes”, Cong et al, provides key insights into such attacks and cite sources which estimate the global damages from ransomware attacks will reach 30B USD by 2023 (https://wp.lancs.ac.uk/finec2023/files/2023/01/FEC-2023-017-Daniel-Rabetti.pdf). We use this and other sources coupled with our own insights in utilizing a commercial blockchain analytics tool from Elliptic to present a ransomware primer and insights into the economic activity associated with such attacks.
Stages of attack
The groups that carry out ransomware attacks follow a set pattern of behaviours, hence knowing their identity would indicate their methods in various stages of an attack. This would also reveal, for example, the types of tools they use to, gain initial access into the external network and then to the internal network, laterally move around in the internal network, escalate privileges within the internal network, scan internal network infrastructure and exfiltrate data.
Once these stages are executed the attacker encrypts the victims files using a key known only to them, making these files effectively useless as they can no longer be read by the victim’s systems. The attackers then attempt to extort value from the victim in return for access to a tool which can be used to decrypt the files and them useful again. Having had operations incapacitated by the loss of access to critical files the victim is faced with the choice of paying the ransom or attempting to restore their information systems from uninfected backups.
The threat of leaking data
Cong et al, notes that since 2019 a new trend of double extortion is in play where the attacker may hold additional leverage over the victim via threats to leak unencrypted files onto the dark web. At a minimum, this would be a source of embarrassment and reputational damage to the victim should the security breach become known to the public via such a leak. Data privacy of employees, clients and supply chain vendors may all be at risk should such a public exposure of data take place.
We know exactly what this looks like in the wake of the recent incident at TSTT which was carried out by the RansomEXX group where there was open public discussion of the contents of the data dump with Personal Identifiable Information (PII) of clients of the victim being exposed. The authors would like to emphasize that responsible disclosure from professionals who handle and report on such data is expected, such that victims and their stakeholders are not further aggrieved by details of their data being openly discussed in public fora. Methods to obfuscate PII of victims should be employed in reporting such incidents.
Ransom demand and possible payment
Payment is demanded in crypto currency, such as Bitcoin, given that it is easily transferable across the Internet and avoids cross-border currency challenges. Negotiations may be involved where an incident response team is hired by the victim to lend expertise and attempt to buy time and lower the ransom amount being demanded. The decision to pay is up to the victim; however, sanctions lists may play a part in the decision making process. In the case of the ransomware group Conti, after publicly declaring their allegiance to Russia in 2022, post invasion of Ukraine, potential payments to Conti took on an illicit nature given Russia’s sanctioned status. Eventually, Conti had to close up shop, but affiliates of the group are suspected to still be operating.
Blockchain Analytics In Ransomware
Once the payment is fulfilled the victim should receive decryption tools which they can use to decrypt their encrypted files; however this is not guaranteed. From the leaks which eventually follow ransomware attacks, we can infer that not all victims pay. When payment does occur the possibility exists to follow the crypto currency trail to wallets associated with the ransomware group and their affiliates.
The FBI was able to utilize blockchain analytics as part of its investigation to trace the 75 Bitcoin which was paid to Darkside in 2021 and eventually recovered 63.7 Bitcoin or 2.3M USD. This payment was related to the Colonial Pipeline attack which resulted the halting of 5500 miles of pipeline operations ultimately negatively affecting consumers on the eastern seaboard and causing a state of emergency to be declared in more than 17 US states. 45% of pipeline operation in the US was affected.
REvil/Sodinokibi
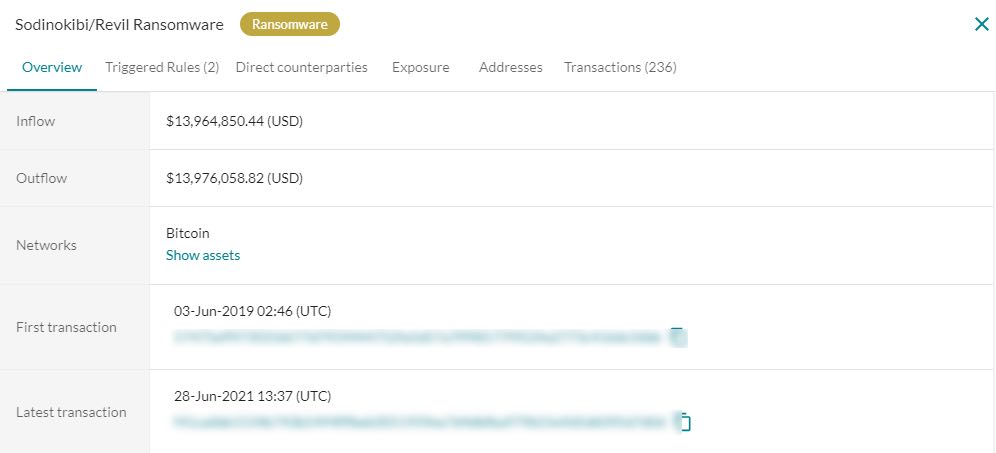
In 2020, the ransomware group REvil/Sodinokibi evaded security measures employed at ANSA McAL affecting operations in both Trinidad and Tobago and Barbados. Using a commercial blockchain analytics tool from Elliptic we can see a cluster of wallet addresses on the Bitcoin network associated with REvil/Sodinokibi, which reveals activity going back to 2019 when the group was formed.
The value attributed to this particular cluster of wallets shows inflows of 14M USD and outflows of 13.9M USD from first transaction in June 2019 to the latest transaction in June 2021. Cong et al, attributes 282 victims to the REvil/Sodinokibi group over the period May 2020 to June 2021. They further estimate that the total USD value received by this group, for the period 2021 to 2022, places them fourth overall in terms of ransomware groups receiving such value. For the same period, the Conti group is number one, estimated to have received 50.9M USD.
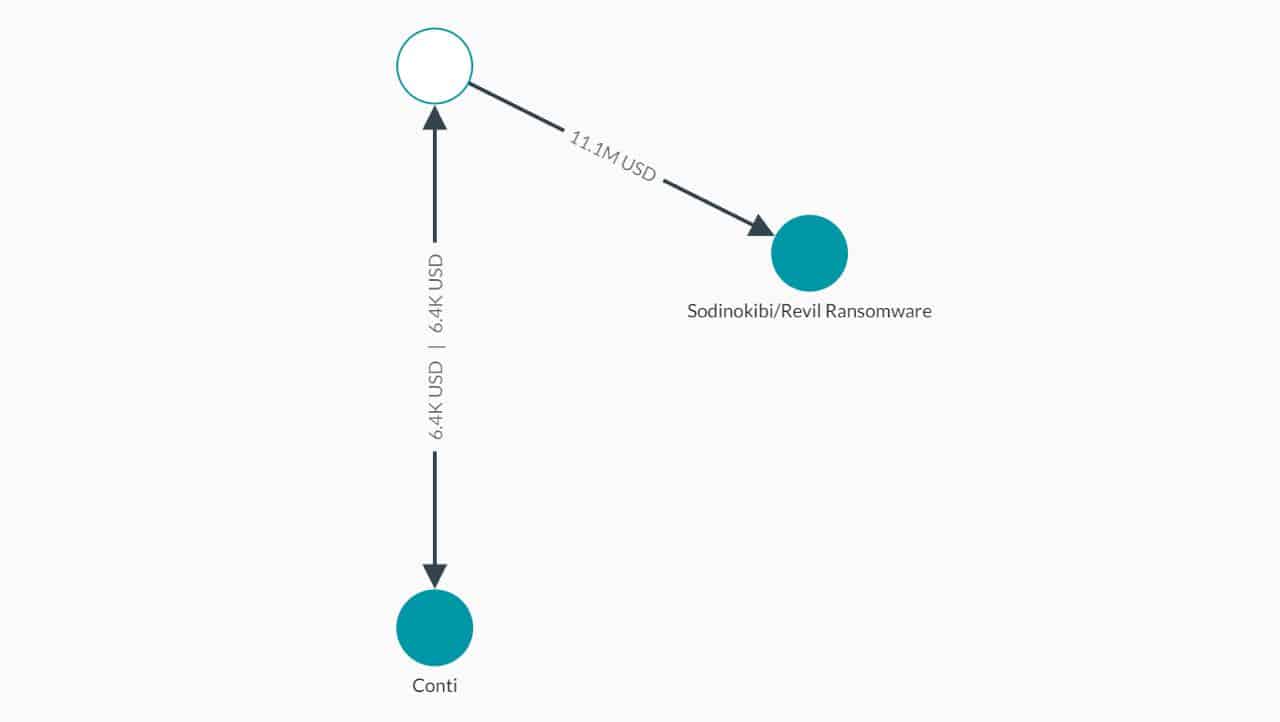
If we look at some of the illicit activity identified within the Elliptic tool attributable to REvil/Sodinokibi we can highlight an 11M USD transaction from an unknown source which also had a simultaneous but much smaller 6.4K USD transaction with Conti.
On a global scale, ransomware actors are seen a serious threat to operations which rely on the Internet. In November 2021, an international law enforcement effort, carried out by 17 countries and including INTERPOL, called Operation GoldDust, resulted in the take down of REvil/Sodinokibi ransomware group and its infrastructure. Almost simultaneously, the US Department of Justice issued a 10M USD reward for information leading to the capture of leaders of REvil/Sodinokibi.
Conclusion
While seemingly defunct now, we should be concerned that the fourth largest ransomware group for 2021 to 2022 executed an attack on a large Caribbean conglomerate. The increasing number cyber incidents that we are seeing on larger entities should lead us to be apprehensive over what may be taking place at small and medium enterprises. The most recent attack by RansomEXX on TSTT is also cause for trepidation as according to TrendMicro, this group is known to specifically target its victims; evidence of this pre-planning being the victim’s names found hardcoded in binaries during post attack forensics.
These concerns must be recognized by corporate entities as they prepare their response to the increasing risk of cyber incident. Having a dedicated Information Security function within your organisation which can pay attention to not just technology, but the people and process dimensions as well, is a requirement. Awareness must be built from the ground all the way up to the C-Suite and board members as the initial access into a network can be a phishing email.
In the wake of the Colonial Pipeline incident an executive order was issued in the US demanding greater attention to national cybersecurity. Would these threats be recognised locally at the national level given these attacks can cripple critical infrastructure?
Should this be our Colonial Pipeline moment?




























[…] Caribbean – What do the following entities have in common; ANSA McAL, Massy Group, Beacon Insurance, Attorney General’s Office Trinidad and Tobago and Telecommunications Services of Trinidad and Tobago (TSTT)? Since 2020, they’ve all fallen victim to cyber incident which resulted in impact to their service delivery. At least three of these entities have confirmed their incident was ransomware related… more […]