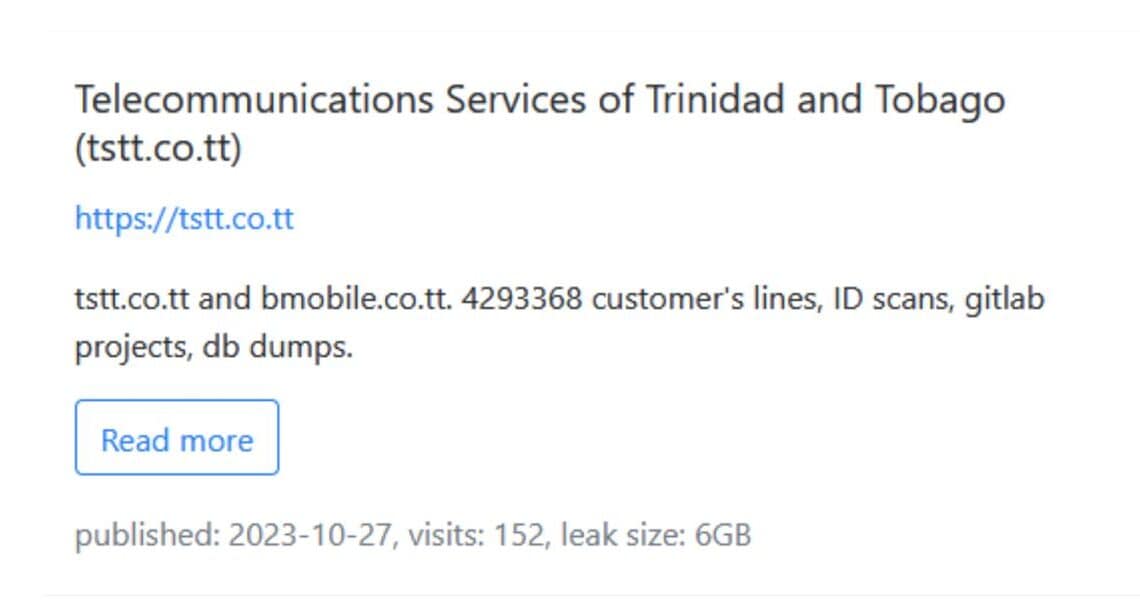
Above: FalconFeeds’s summary of the TSTT exploit, published on its Twitter feed yesterday. (Thanks to the TTCS for the heads up)
Multiple data breach reporting sites have noted a compromise and exfiltration of data from the systems of the Telecommunications Services of Trinidad and Tobago (TSTT) on October 27, 2023.
According to FalconFeeds.IO, a cybersecurity firm that offers a Twitter feed reporting on breaches, tstt.co.tt and bmobile.co.tt were compromised, with a reported 6GB of customer lines, ID scans, gitlab projects and database dumps as part of the haul.
RansomEXX was introduced as Defray777 in 2018 and became particularly notable when it was used in high-profile exploits on government agencies and manufacturers. As ransomware, it remains notable among other notorious names such as Lockbit and Conti and is known for publishing the data stolen from government agencies.
According to the Ransom_db tracker, RansomEXX is a midrange exploit with a victim count of 56 when this report went live.
More information about the exploit can be found in this TrendMicro post.
When RansomEXX attacked a Scottish mental health charity in March 2022, the group using the exploit thought nothing of publishing 12GB of personally identifiable data (PII), including credit card details.
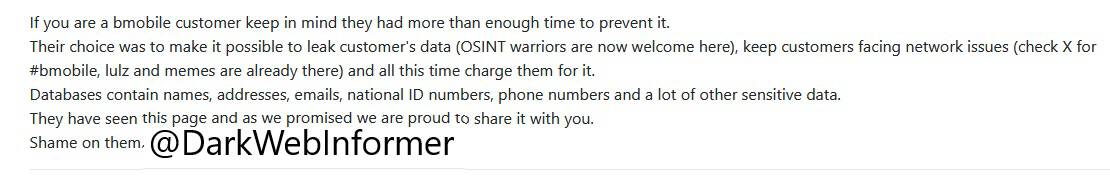
Update (October 28, 2023): The Dark Web Informer, a breach reporting Twitter feed surfaced a note from the Defray777 name and shame website that alleges that TSTT was warned of the consequences of non-compliance with demands before the release of data on October 27. The channel posted a screen shot, allegedly from the Defray777 page which stated…
“If you are a mobile customer keep in mind they had more than enough time to prevent it. Their choice was to make it possible to leak customer’s data (OSINT warriors are now welcome here), keep customers facing network issues (check X for #bmobile, lulz and memes are already there) and all this time charge them for it. Databases contain names, addresses, emails, national ID numbers, phone numbers and a lot of other sensitive data.
They have seen this page and as we promised we are proud to share it with you.
Shame on them.”
Update (October 29, 2023): The proof of data exfiltration page posted by RansomEXX accessed using the Tor browser offers links to the following files in 7z archive format, two Oracle customer information database files 25.9MB and 196MB in size, 267MB of customer ID scans, an 82.5MB “credentials” file and a 61.2MB GitHub archive that was stored locally on TSTT’s servers.
One of the proof files is a detailed CSV file listing detailed customer information for more than 800,000 TSTT customers.
This is not the complete data dump, just a selection of items intended to prove to TSTT’s IT team that RansomEXX actually has the data it claims to have exfiltrated. This proof package would have been sent to TSTT anywhere between 30-90 days before the data dump if the ransomware group followed established protocols for warning hacked clients and demanding payment. The proof page onion site was viewed using the Tor browser and following a link provided by a cybersecurity professional.
Update (October 30, 2023): At 5:55pm on October 30, TSTT issued the following press release regarding the hack of its servers…
On October 09, 2023, cyber attackers attempted to gain unauthorised access to TSTT’s systems. Cyber threats of this nature are a continuous feature of modern digital operating systems and telecommunications infrastructure is no exception to these threats and incursions. TSTT has continuously invested resources in the millions of dollars in its processes and IT infrastructure to protect its systems and the data it produces and stores.
At the onset of the threat, TSTT’s incident response processes were swiftly activated. The company took immediate steps to minimise the security vulnerability, successfully isolating its systems and applications. These applications were subsequently quarantined, rebuilt and put back into production as part of clearly defined policies and procedures.
The company also enlisted the support of internationally recognised cyber security experts and partners in investigating the attempted breach and advising on the implementation of appropriate additional security measures and protocols. Some of these recommendations have already been implemented.
The company’s cyber security processes operated optimally and were able to restrict these criminals’ malicious plans. There was no loss or compromise of customer data, i.e, no data was deleted from TSTT’s databases or manipulated. At this time, the company has not corroborated data currently in the public domain purported to be TSTT’s customer information, and it should be noted that the various TSTT platforms generate terabytes of data.
TSTT strongly condemns the actions of these terrorists in unlawfully attempting to gain access to its customers’ information. The company will continue to invest in hardening its IT environments under the guidance of international cyber experts, to ensure the security of customer information.
In its press release, TSTT does not deny that data was exfiltrated from its servers, only that data was not deleted, manipulated or lost. This aligns with normal ransomware practice. First the data is exfiltrated, then the data on the company’s servers is encrypted and a threat to release the data is issued to create greater motivation for payment.
It is unclear whether October 09 is the date on which the ransomware was activated or the date on which the company detected intrusions into its systems. Noting that the company generates terabytes of data is a straw man tactic to draw attention from the specifics and seriousness of the exfiltration. What matters is which 6GB of data the company has had copied off its servers.
TSTT has the expertise and the manpower to examine the proof of exfiltration data posted to the darkweb and must be aware that customer credit card and other personally identifiable information has been in the wind for weeks. It must also be aware of the contents of the 6GB file that was released by RansomEXX.
It is unclear what Minister of Public Utilities Marvin Gonzales has been informed is untrue about the reporting on this incident so far. If TSTT has not, in fact, corroborated the existence of customer data freely available on the darkweb at this point, it is either trading in semantics or incompetence.
Ordinary citizens will not be able to readily access this company information with the ease of a Google search, but TSTT does not have to worry about ordinary citizens. Its response to what it describes as terrorism and the danger posed by the data exposed in this breach cannot be mollified by the chest beating exercise articulated in its October 30 press release.
TSTT has not acknowledged the data breach, the release of customer information or the scope of the data now on the darkweb, nor has it warned its customers about possible issues that may result from the availability of this data.
The Ministry of National Security’s Cyber Security Incident Response Team (TT-CSIRT) has issued no advisories to the public regarding the breach 21 days after TSTT detected it and 48 hours after knowledge of the data dump had been released on the public internet.
Update (November 01, 2023): An independent review of the data dump suggests that a files of internal system passwords and external customer passwords were part of the data package exfiltrated from the company’s servers. It appears that these files were stored unencrypted and in plain text file dumps.
TSTT has had days to examine the data that is, as it acknowledged in its press release, is in the public domain, but has not advised whether it has warned business customers of their exposure in this breach. The company continues to make no effort to issue any warnings to its over-the-counter customer base about exposure of their personally identifiable information.
Data Protection consultant Rishi Maharaj has offered concerns about the issues arising from this exposure. At this point, the entire issue appears to be subject to the Law of Triviality. The complexity of the issues arising are simply much harder to consider than arguing about, for instance, whether Tobago Carnival was good this year.
Since TSTT won’t say it, I will.
If you have an account with TSTT for payments, change your password immediately.
If you do business with TSTT as a company, change all your access passwords immediately and have a discussion with company representatives about your exposure.
Update (November 04): I’ve had some requests from friends who want to find out what’s in the TSTT data dumped to the darkweb by RansomEXX. There are several files, the most notable of which are an ID file, listing customer identification information with 377,164 records, a contacts file with 800,977 records, a file with employee IDs and passwords with 158,032 records and an Oracle database Customers file with 4,293,368 records.
File sizes are slightly deceptive, since some customers are listed multiple times with different information associated with them or duplicate information, but the overall count is massive.
It’s important to note that while a spreadsheet is a database, a sophisticated database is not a spreadsheet. As a consequence, the way some of these files open in a spreadsheet is not the way it will be read into a database file.
The customers file, for example, quickly hits the upper limit of a spreadsheet’s capabilities. Apple’s Numbers stalls out at one million records while Excel coughs up a lung at just shy of 1.5 million. Neither app could open the full customer database.

The other numbers are internal customer relations ranking information.
In addition, columns in the file aren’t read properly and are conflated into near unreadability. It’s possible to tease the information – which lists internal customer ranking and status information – out of the file, but without loading it into a compatible database, the file is unusable to the casual browser.
A moderately talented spreadsheet/database jockey should be able to knit this information together to amass a surprisingly detailed profile of the customers in this data.
TSTT has characterised this information as being equivalent to the information to be found in a phone directory. That is absurd, A phone directory is not malleable information that can be matched with other datasets. It also does not contain bank account information or personal ID information.























[…] Trinidad and Tobago – Multiple data breach reporting sites have noted a compromise and exfiltration of data from the systems of the Telecommunications Services of Trinidad and Tobago (TSTT) on October 27, 2023… more […]
[…] customers of tech users registered with Telecommunications Services of Trinidad and Tobago (TSTT) received scary news of a ransomware attack on the company. Local tech journalist Mark Lyndersay, writing at […]