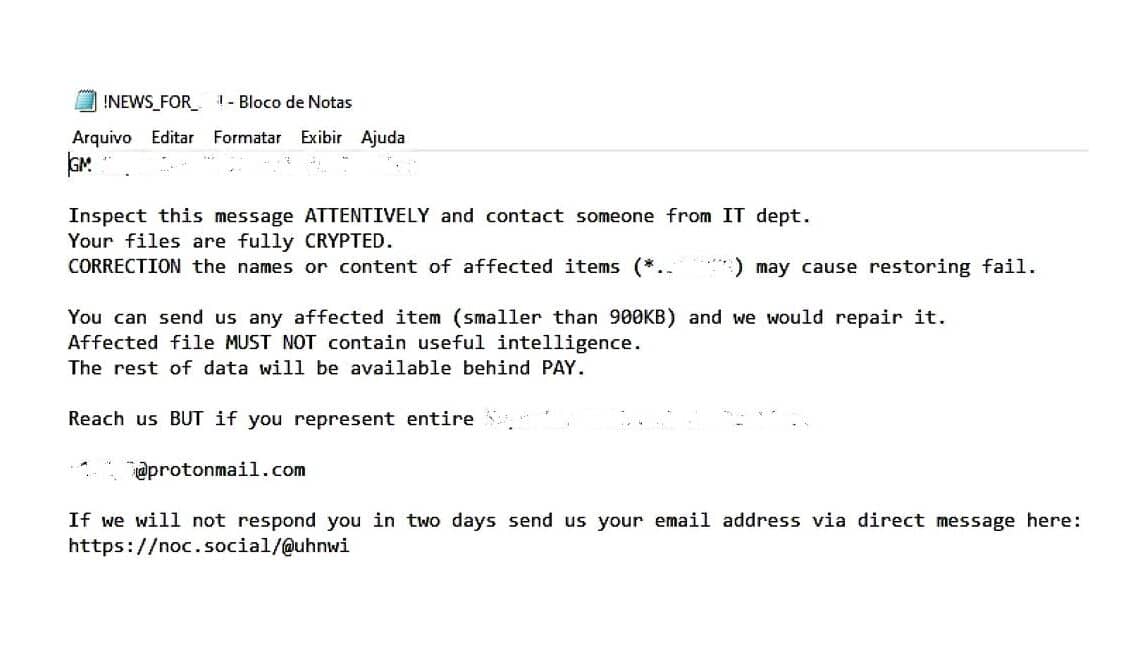
AboveL A redacted note issued by RansomEXX
Shiva Parasram created this list of factoids about the ransomware group RansomEXX and published it to his LinkedIn page. It is reproduced here with his kind permission.
- 🎯 Emergence: RansomEXX came into the spotlight around 2020, primarily targeting notable organizations.
- 📛 Alias: They are also referred to as Defray777, stemming from a unique identifier in their ransomware code.
- 🔒 Encryption Techniques: RansomEXX employs strong encryption, making it difficult to restore files without their decryptor.
- 🌎 Global Attacks: While selective, they have targeted entities across various continents.
- 🔍 Specific Targets: They have a penchant for large corporations and public sector organizations.
- 🖥️ Hands-on Approach: RansomEXX prefers manual operations inside a network over automated techniques.
- 💽 Data Theft: Before encrypting systems, they often steal sensitive data.
- 📢 Double Extortion: They not only encrypt but threaten to leak stolen data if ransoms aren’t paid.
- 📜 Personalized Notes: Their ransom communications are typically customized based on the victim.
- 💰 RaaS: They do operate independently but have been known to operate as a RaaS (Ransomware-as-a-Service) model.
- 🎣 Phishing Mastery: Deceptive emails are often their initial entry method into networks.
- 🔗 Exploit Chains: They often chain together multiple software vulnerabilities for deeper access.
- 🖇️ Unpatched Software: RansomEXX capitalizes on outdated and vulnerable software, especially public-facing applications.
- 🧰 Diverse Toolkit: Their arsenal includes a mix of custom and off-the-shelf tools.
- 🔑 Mimikatz: A favored tool for credential dumping and privilege escalation.
- ⚡ PowerShell Empire: A post-exploitation framework granting wide-ranging capabilities.
- 💼 Cobalt Strike: Originally a legitimate pen-testing tool, it’s now a favorite among attackers.
- 🌐 Lateral Tactics: Tools like PsExec help them traverse laterally across compromised networks.
- 🔍 Network Recon: They actively map networks using tools like BloodHound.
- ☁️ Data Movement: Rclone can be misused for moving data stealthily to cloud storage.
- 🔍 Active Directory: They mine AD data using tools like AdFind for understanding permissions and relations.
- 🚪 Misconfigurations: They exploit insecure settings or exposed services.
- 📊 Target Research: Before an attack, they spend time researching potential victims for maximum impact.
- 💰 High Ransoms: Their demands can be exorbitant, reflecting their target’s perceived ability to pay.
- 📈 Tailored Operations: RansomEXX customizes their attack methods based on the target’s environment.
- 🛡️ Avoiding Detection: They use “living off the land” tactics to blend into environments.
- 🚷 No Known Decryptor: As of the last known update, no public decryption tool can counter RansomEXX.
- 📞 Communication Channels: They often provide a communication channel for ransom negotiations.
- 🔥 Destruction: In some cases, they may try to delete backups or disrupt recovery efforts.
- 🌍 Varied Victims: Targets have included healthcare, government entities, and critical infrastructure.
- 🔄 Network Propagation: Once inside, they work to gain higher privileges and access more systems.
- 🔐 Credential Theft: Capturing credentials is a priority to facilitate movement and persistence.
- 🛑 Stopping Security: They might attempt to disable security software or services.
- 🗂️ File Types: They target a broad range of file extensions, ensuring vital data gets encrypted.
- ⌛ Dwell Time: They can remain in networks for days to weeks before launching the ransomware.
- 📝 Detailed Notes: Ransom notes often provide detailed payment instructions using cryptocurrencies.
- ⚖️ Negotiations: Some victims have successfully negotiated lower ransoms.
- 🚫 Decryption Issues: Even after payment, decryption isn’t always smooth, with occasional technical issues.
- 🌐 Network Disruptions: Their operations can disrupt not just endpoints but entire networks.
- 🚫 No Warranty: Paying the ransom doesn’t guarantee data safety or prevent future attacks.
- 🕵️ Stealth: They often clean logs or use encrypted channels to avoid detection.
- 📦 Payload Delivery: Various methods, from malicious attachments to drive-by downloads, are used.
- 📡 Command & Control: They establish robust C2 communications to control compromised systems.
- 🛡️ Backup Importance: The best defense against their attack is having secure and isolated backups.
- 🚫 No Discrimination: Despite being selective, no industry is truly safe from their attention.
- 🖲️ VPN Exploits: Vulnerable VPNs have been a notable point of entry.
- 📅 Continuous Evolution: Their techniques and tools evolve to counteract defenses.
- 💡 Awareness: Training staff to spot phishing and suspicious behavior can prevent initial access.
- 🚀 Rapid Response: Quick detection and response can mitigate the damage they cause.
- 🔒 Layered Defense: Employing a multi-layered security approach is crucial in defending against groups like RansomEXX.





















