
Above: Illustration by Chayanaelexir/DepositPhotos.
BitDepth#1381 for November 21, 2022
Between November first and third, the American Chamber of Commerce in Trinidad held its annual HSSE awards event, but in a room off to the side of the main health and safety conversations and awards, a small group of IT professionals talked cybersecurity.
This parallel elevation of data safety to danger management levels wasn’t as out of place as it might seem.
A growing awareness of the threat of data breaches to both business continuity and to personal safety as hackers steal and distribute deep caches of personally identifiable information (PII) was sensibly raised by AMCHAM to top level corporate concern.
The numbers are staggering.
According to Sem Ponnambalam, CEO and founder of cybersecurity company xahive, software supply chain attacks hit three out of five companies in 2021.
The SolarWinds software supply chain attack happened after 18,000 downloads of the SUNBURST malware, though less than 100 were hacked through the exploit.
There was a ransomware attack launched against a company every 11 seconds in 2021. By 2030, the frequency of those attacks is expected to come every two seconds.
And even these intimidating numbers may be underestimated.
“A lot of the time, the incidents are not reported,” Ponnambalam said.
“While the default position is to refuse paying to release data encrypted in a ransomware attack,” said Marcelo Ardiles, cybersecurity consultant at Hitatchi Systems, “globally, 38 per cent of organisations who suffered such attacks paid up.”
Of those who paid, 61 per cent did so to avoid downtime. Another 53 percent paid to avoid reputation damage and 53 per cent paid from ransomware insurance.
The average payout since Q3 in 2021 is US$322,000. Companies are targeted according to their revenue and crypto crimes are estimated to cost $30 billion in losses by 2025.
Angus Smith, manager of the TT Cybersecurity Incident Response Team (TTCSIRT) noted that the agency, convened in 2010 and brought into operation in 2017, is essentially hamstrung by the lack of effective legislation available.
Without effective proclamation of the Cybercrime Bill of 2017 (which ran into issues with media practitioners who objected to wording that limited the practice of journalism) and the National Cybersecurity Agency Bill, there can be no effective governance and coordinated incident management of cybersecurity breaches.
Under current law, it’s not even clear if some modern security breaches are even recognised as crimes by the wording of existing law, the twelve-year-old Computer Misuse Act, a relic of ancient expectations of computer technology abuse.
Current government strategy is to amend the Computer Misuse Act to align with the second protocol of the Budapest Convention, which harmonises baseline computer crime legislation across different nations to reduce the jurisdictional issues that don’t stop hackers.
No data commissioner has been appointed in Trinidad and Tobago, so many crucial elements of the country’s cybersecurity response can’t be implemented and the creation of the proposed National Cybersecurity Policy Framework seems ever more remote.
The framework is supposed to oversee the establishment and implementation of the Critical Information Infrastructure Bill, National Crisis Communication Plan, empower the data commissioner to enforce mandatory reporting of cybersecurity events, breach notifications and vulnerability disclosures as part of a National Cyber Crime Strategy.
Without a coordinated response from the public and private sector, hackers continue to operate at a significant advantage.
There’s already been clear warning of what can happen when countries don’t get their cybersecurity act together.
Costa Rica had to declare a state of emergency and resort to paper documents after an attack by the ransomware gang Conti – demanding US$20 million – shut down tax and customs offices, utilities and other public services in April.
A secondary attack by the Hive ransomware group crippled public health services and systems. Prescriptions could not be filled, and workers went weeks without a paycheck.

Anish Bachu, cybersecurity analyst with TTCSIRT noted that the top hacking group targeting Caribbean systems is Lockbit and many attacks are coming through improperly configured firewalls, unpatched vulnerabilities in software and compromised user credentials.
“Trinidad and Tobago is under attack on a daily basis,” Bachu said.
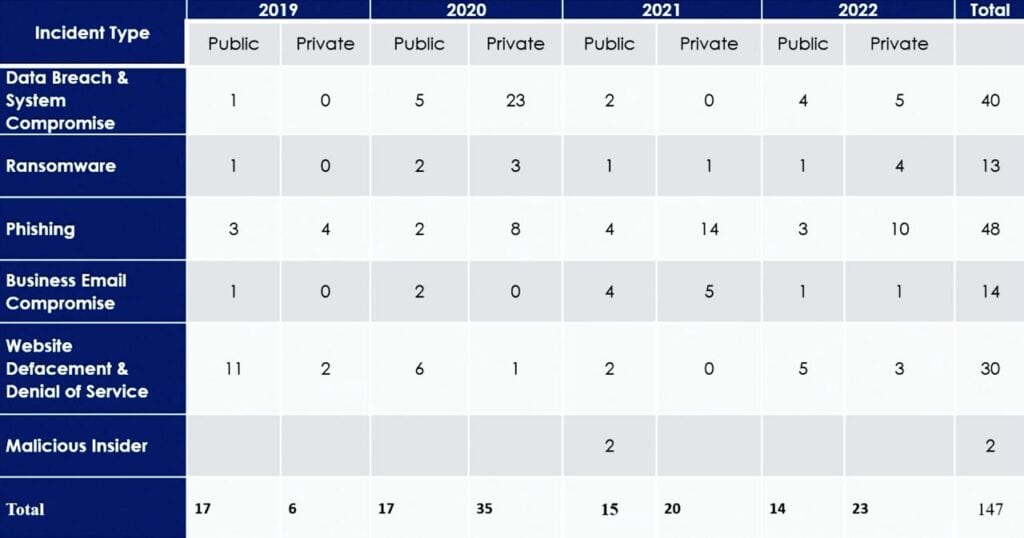
Between 2019 and 2022, the TTCSIRT recorded 48 phishing attacks, 40 data breaches and system compromises and 13 ransomware attacks.
Citing one real world example of a local ransomware attack on an unnamed company, Bachu explained that all the company’s data and backups were encrypted by the ransomware group.
The company partially restored from a years-old off-line backup and had to revert to manual processes, rebuilding the business from paper documents and data sourced from suppliers.
The company has been working for months to recover its business data.
Next week: How a ransomware attack happens and how you can prepare for it.


