
Illustration by booblgum/123RF.com
BitDepth#1378 for October 31, 2022
There was a moment, while working on this story, that I hesitated.
I’d invested some effort – but not that much, really – into exploring the status of the data dump of sensitive corporate information exfiltrated by Hive Ransomware from Massy Distribution.
Now, THE download was running.
A compressed Zip file clocking in at 216GB of company information, legal documents, personnel records and other personally identifiable information (PII) that the ransomware group had first downloaded from Massy and then encrypted on its servers.
I had the onionsite URL to the data on the darkweb. I had confirmed that the data was live and accessible. I had screenshots from a source who had downloaded the file and confirmed the contents.
But how far should a journalist go in search of the story? Did I want or need this information on my computer? What were the legal implications of that?
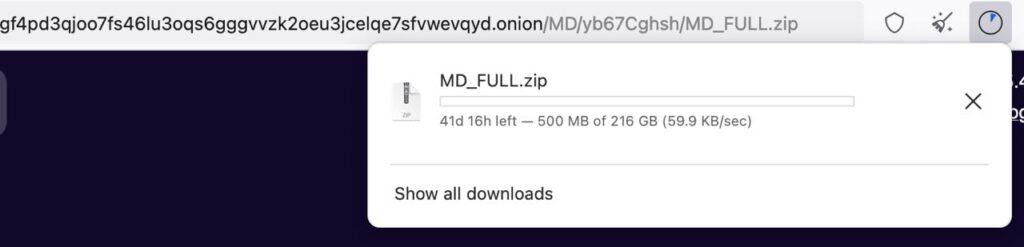
A half-day into the download, with 1GB of data pulled down and at least eight more days to go, I terminated the download and the temporary data file evaporated.
There was too much about this that seemed untidy, gray and frankly, criminal to continue.
It didn’t feel right, but then, neither did Massy’s continuously ignoring repeated requests to interview relevant members of their IT team and get the story from their side.
An insistent stonewalling of media investigation into data breaches has become the norm in Trinidad and Tobago.
I know of four major ransomware breaches in this country; only three of which (ANSA and the PoS City Hall are the others) have been reported.
In all four instances, executives declined to discuss the matter in any depth, preferring legally safe PR denials of any customer or business impact.
Last week, Massy issued a press release that described reporting on the incident as “speculative and inaccurate.”
It was not. If anything, it was excessively cautious and responsible, as you might expect when discussing the business of a major advertiser.
As a consequence of this approach, customers have no clear sense of the exposure of their PII to bad actors. There is no apparent collaboration between IT managers on best practices in handling cybersecurity and there’s a pervasive sense of, “I sorry for you, but I glad it ent me.”
This does nothing to harden digital attack surfaces of local businesses, build an understanding of how these data breaches are being perpetrated or shape a collective ability to respond to these crisis situations when they occur.
On April 28, Massy Stores reported disruptions to their capacity to serve customers and eventually explained that the cause was a data breach. The company insisted that customer information was not at risk.
Red Packet Security noted on July 12 that Hive had posted data related to the breach online.
In the evolving ransomware landscape, hackers prefer a double-barrelled assault. Having gained access to a company’s systems, malware will infiltrate as far as it can while surreptitiously downloading what it finds to darkweb servers.
Then the malware encrypts the data accessible to it on the company’s servers and a ransom is demanded, normally payable in Bitcoin.


Payment to release the encryption may or may not include a promise to delete the exfiltrated data, but sensible people shouldn’t trust the word of criminals.
A “proof pack” of the Massy data revealed that the company’s business information was in the wind, but it wasn’t until September 19 that the full dataset was dumped to the dark web.
According to a source, “The files are provided by the hackers in a compressed Zip folder with a size of 216.1 GB that contains the company’s files. When uncompressed or unzipped that file size is much larger.”
“By October 18, the hackers had removed the webpage that provides the link; however, the direct link to the files on their web servers is still accessible so the files can still be downloaded by anyone with the link. It would take someone approximately 7-8 days to download the entire compressed zip folder.”
The source, who has viewed the data dump, explained that the Zip archive contains, 87,550 folders containing 704,047 files.
“Included are financial records (accounts receivable, accounts payable, budgets, banking, financial statements, internal audits), human resource records (staff photos, surveys, staff listing, job descriptions, events, claims) and operations information.”
What are the consequences of this information becoming available to bad actors? Identity theft, exposure of PII and sensitive corporate data are just a few potential liabilities. Employees of Massy Distribution should be extremely concerned at this point.
On October 08, Massy Distribution Jamaica reported a data breach and the following day, a 17 GB cache of the Jamaican company’s data was dumped on the darkweb.
Unlike TT, Jamaica’s laws specify exactly what a company must do after discovering a breach.
The TT Cybersecurity Incident Response Team responded to questions about what’s expected of local companies and agencies in the wake of a data breach.
“There is no enacted law that compels a public or private entity to reveal details of a data breach,” an unattributed response from the cybersecurity agency explained.
The TT-CSIRT said that it contacted Massy after the April incident and was supplied with a copy of the media release.
“The TT-CSIRT does not have the legal authority to initiate a criminal investigation (this is the responsibility of the TTPS Cyber and Social Media Unit), nor does it have the authority to initiate investigations under the Data Protection Act (that is the responsibility of the Office of the Information Commissioner – which has not been established).”
The TT-CSIRT said that it contacted Massy after the April incident and was supplied with a copy of the media release.
In July, TT-CSIRT reviewed the proof pack. The agency then unofficially offered Massy advice based on their investigation of the October data dump.
“The TT-CSIRT does not have the legal authority to force any private entity to comply with its guidance. Any entity has a duty to its employees and the people they serve.”
“It is the civil responsibility of the entity to assess the extent of the breach, determine and notify the affected parties and provide a mechanism which can assist affected persons to monitor their information for identity theft.”

