
Above: Jeremy Dallman. Photo from his LinkedIn page.
BitDepth#1369 for August 29, 2022
At an online security briefing on Wednesday, Jeremy Dallman, Senior Director at the Microsoft Threat Intelligence Center (MSTIC, pronounced “mystic”) elaborated on the cybersecurity threats that the company reports on in the second edition of its Cyber Signals threat evaluation.
MSTIC is not a product, though its findings help to inform Microsoft’s responses to threats in its products.
Intelligence gathering is done through its own networks and through industry collaboration, including its competitors.
“We may compete with our products,” Dallman said, “but we are all dealing with the same threats.”
The threat evaluation division engages in “hunting,” the analysis of attack vectors and techniques to builds profiles of the actors involved in these digital threats.
Microsoft is currently processing 24 trillion signals per day, gathered from multiple sources of intelligence.
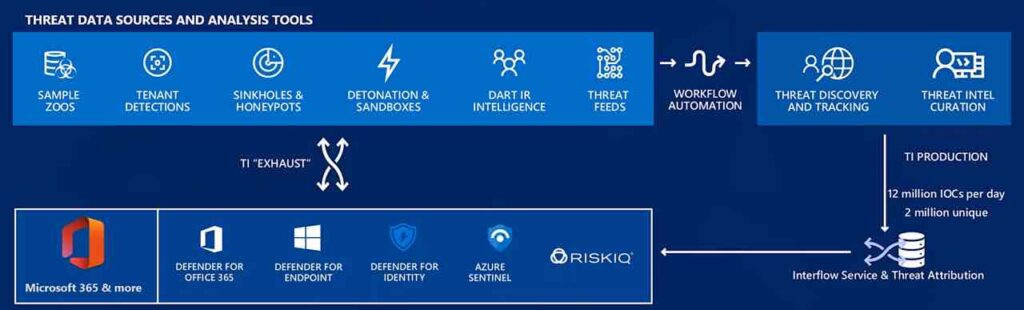
To handle this brobdingnagian dataset, the company correlates it using big data management techniques and machine learning evaluation.
The company has automated the checking of links in suspect emails on its networks, after finding that 95 per cent of threats begin with an email lure, and quarantining potential spam emails that target unsavvy users.
Knotweed, a new malware package deployed in Europe, is embedded in meme images and deploys when the file is loaded.
User inertia is also a factor. An analysis of 45 days of signals revealed that 20 million internet connected devices were using the default password, “admin.”
The end goal driving most compromised systems and unauthorised access is ransomware, which Microsoft describes as having evolved an “extortion economics” model.
The Ransomware as a Service (RaaS) model offers tools provided by developers of malware to affiliates who then use these products to lock down compromised computer systems.
MSTIC estimates that some of these programs have more than 50 “affiliates” who use these RaaS kits with varying levels of skill and success.
MSTIC has found three distinct players involved in this new business of breaking computer security systems.
An access broker will use phishing techniques to gain access to a computer system. A RaaS affiliate will buy tools to exploit this access for a 30 per cent cut of the profit, paying a fee starting at US $250 to an access broker if they are not a part of the affiliate’s business. Stolen username and password pairs sell for around US $150 for 400 million.
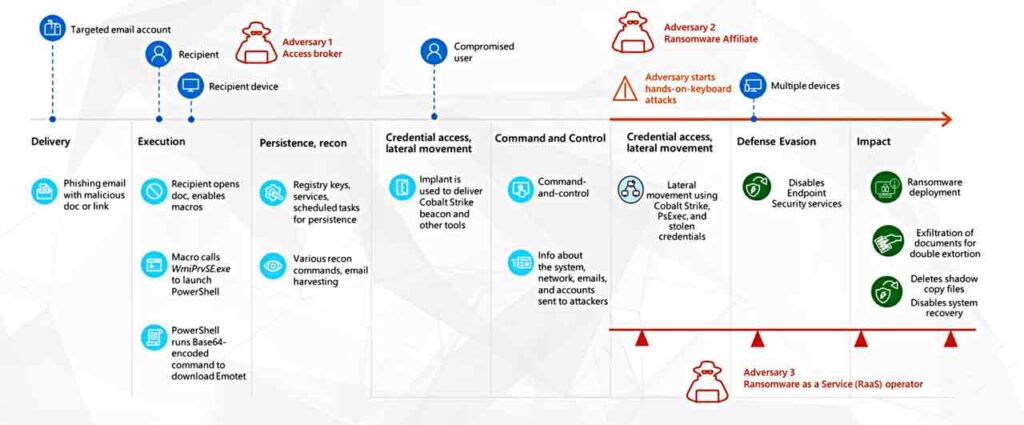
Compare the cost of these attacks with the business cost.
The FBI found in 2021 (PDF) that cybercrime cost the US a hefty $6.9 billion while the EU’s cybersecurity agency estimates that ten terabytes of data are stolen each month through ransomware.
More than half of that stolen data includes employees’ personally identifiable information.
Microsoft tracks 250 groups involved in malicious attacks on computer networks. The company has identified 80 so-called “element” groups, state-sponsored malicious organisations, which it renames according to the periodic table.
At least eighteen of these gangs are actively targeting Asia and Europe, operating primarily out of Iran, Russia, Turkey, China, North Korea and Vietnam.
There are six “volcano” groups, human operated ransomware groups involved in high-impact financial crime. Private sector offensive actors are businesses that develop and sell hacking tools.
One actor, Sourgum, is believed to be Israel-based and targets journalists and activists. More than 160 groups are considered to be in their development phase.
Dallman acknowledged that the heat of cybersecurity compromises has tended to focus on North America, Europe and Asia, but noted that Nickel, a group operating out of China has been targeting governments, diplomatic entities, NGO’s and telecommunications organisations in Latin America and Europe.
“Latin America and the Caribbean are facing an increased threat profile,” he said, “and while the biggest rise is in North America, which attracts 48 per cent of attacks along with specialised attacks in Asia, Russian activity is rising in South America.”
The attacks target regional economic interests to pursue espionage, pulling information that is useful in negotiations and has enjoyed high success in compromising targets with unpatched VPN services and internet-facing apps running on-premise Exchange and Sharepoint installations.
In a particularly troubling report on the cybersecurity aspect of the Russian invasion of the Ukraine, Microsoft reports that while Russia was in diplomatic talks in January before the attack, it deployed cyberattacks involving “wipers,” software designed to destroy data on a hard drive and launched distributed denial of service (DDOS) attacks to cripple Ukranian financial institutions.
When diplomatic discussions faltered, cybersecurity attacks were consistently stepped up.
“This is a business ecosystem built around designing effective ransomware attacks,” Dallman said.
He suggested that regional companies and governments should commit to improving cybersecurity measures, update on-premise systems quickly or upgrade to the cloud, where updates and patches can happen at cloud scale and speed.

