Above: Microsoft’s Vasu Jakkal. Photo courtesy Microsoft.
BitDepth#1353 for May 09, 2022
Today, Microsoft unveiled new products and an informative package of blogs and research information on ransomware and cyberattacks that are quite relevant to Trinidad and Tobago.
The recent high profile hack at Massy Stores wasn’t the only cybersecurity breach to happen over the last fortnight.
The websites of both the NESC Technical Institute and TTWeathercentre were hacked within hours of each other.
The NESC site was restored quickly, but TTWeathercentre’s team called a time out on the website to overhaul its design and security.
Kalain Hosein, who manages TTWeathercentre, noted that in October 2019 a possible WordPress brute force attempt took the site down with IPs originating mostly from Russia and the Ukraine.
After that, he implemented Cloudflare, a content delivery network and distributed denial of service (DDoS) protection on the advice of his hosting provider.
The most recent attempt was likely to have been a successful brute force attack (automated guessing of access credentials) from IPs disguised by Tor, China and Greece.
“Cloudflare was enabled and was managing the attacks prior to 2:00 AM when it was scheduled to be temporarily disabled for routine maintenance,” Hosein said.
The site went down at 2:05 am on April 29 and when it was accessible again at 2:17 am, Hosein discovered that at least two-thirds of the website had been destroyed in an act of digital vandalism.
He is currently fortifying security and implementing a redesign of the website, which he hoped to return to service on May 07.
Hosein is rare in openly discussing the issues that he faced after a cyberattack.
Most cybersecurity attacks happen under a veil of misplaced IT omerta; a silence fed by a fear of lost customer confidence and a reluctance to be cross-examined on the value and scope of losses.
The TT Cybersecurity Incident Response Team (TT-CSIRT) issued an advisory on April 29 warning of “increased malicious cyber activity” and urging businesses and individuals to report these incidents.
At least one reason why businesses ignore the TT-CSIRT is that it has severely limited legal powers under existing legislation. Under the Computer Misuse Act, the scope of computer attacks isn’t properly defined, particularly when it comes to modern attack vectors.
And that threat landscape is rapidly evolving.
According to Vasu Jakkal, CVP of Microsoft’s Security, Compliance, Identity and Management Business, speaking at an embargoed announcement of new cybersecurity products on Wednesday, “Customers are dealing with increasingly sophisticated attacks that have grown at an alarming rate over the last year.”
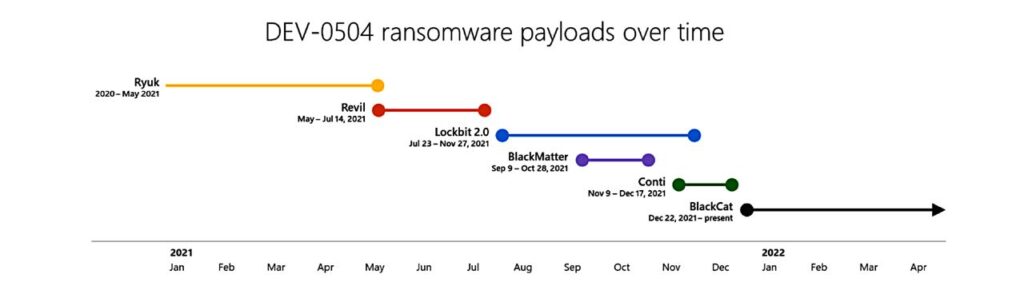
“Microsoft Security is actively tracking more than 35 ransomware groups and the Microsoft Threat Intelligence Centre tracks over 250 unique threat actors across observed nation state, ransomware, and criminal activities.”
“In the last year, we’ve seen an increase in attacks everywhere, our technology blocked 9.6 billion malware threats and more than 35.7 billion phishing and other malicious emails.”
In response, the company has identified cybersecurity as an area of software and service expansion, creating a new business category called Microsoft Security Experts as part of its Security Services for Enterprise business division.
The company emphasises protection based on zero-trust principles to protect identity, endpoints, apps, network, infrastructure and data.
The new products are:
Microsoft Defender Experts for Hunting, which makes specialised cybersecurity expertise available on demand for managing specific incidents or attack vectors.
Microsoft Defender Experts for XDR, a managed extended detection and response service that uses automation and human expertise to respond to incidents. The company sees managed detection and response as the future of cybersecurity postures.
Microsoft Security Services for Incident Response is a service specific to breaches, threatened or in progress for removing malware and improving cybersecurity.
Microsoft Security Services for Modernisation emphasises zero-trust principles and modern practice in the implementation of a forward-looking cybersecurity posture.
Microsoft, which has traditionally worked well with third-party partners, has established the Microsoft Intelligent Security Association with more than 100 managed security service providers and 785,000 customers.
The Microsoft 365 Defender Threat Intelligence Team has authored an startling 20-page assessment of the current cybercrime landscape, “Ransomware-as-a-service: Understanding the cybercrime gig economy and how to protect yourself” that’s required reading for anyone in a management role at a modern, digitally connected company.
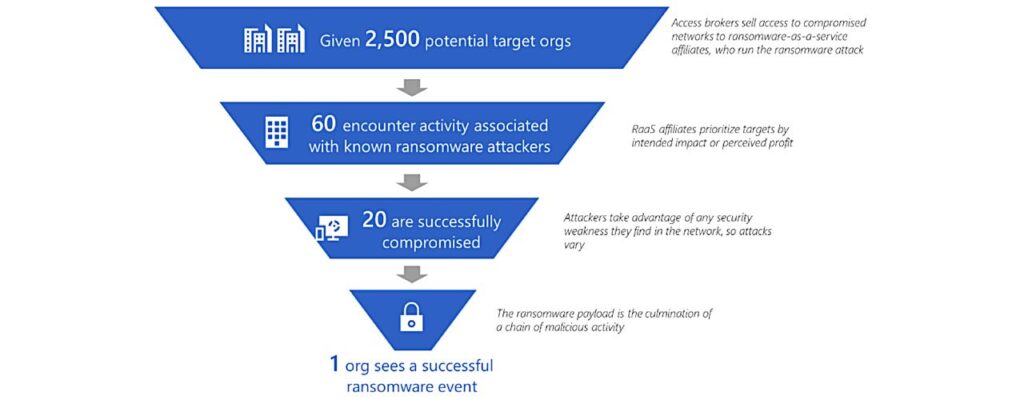
Among the conclusions that the report offers is this chilling assessment: “Most ransomware attackers opportunistically deploy ransomware to whatever network they get access to, and some even purchase access to networks from other cybercriminals.”
“Some attackers prioritise organisations with higher revenues, while some prefer certain industries for the shock value or type of data they can exfiltrate.”
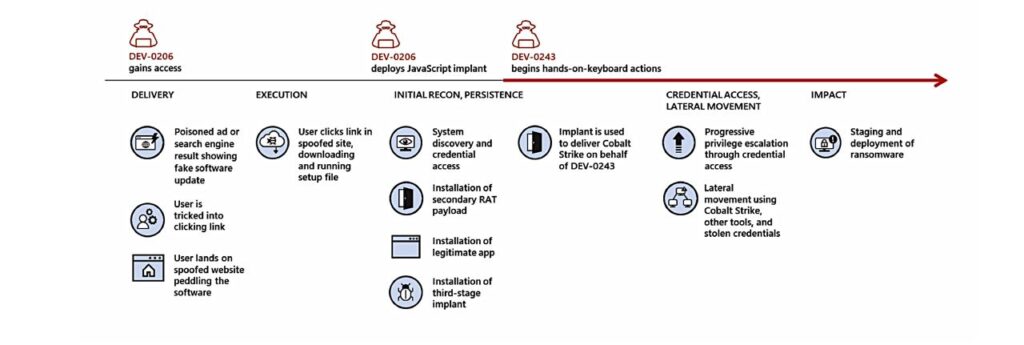
“Unlike the broad targeting and opportunistic approach of earlier ransomware infections,” said Jessica Payne, principal security researcher at Microsoft, “attackers behind these human-operated campaigns make informed and calculated decisions and vary their attack patterns based on what they find in their target’s networks, like discovering a security product isn’t configured to prevent tampering, or a service is running as a highly privileged account.”
“Attackers are often more determined to stay on a network once they gain access and sometimes repeatedly monetise attacks using different malware or ransomware payloads if they aren’t successfully evicted.”