
Updated October 26, 2020…
According to Eric Taylor, a cybersecurity expert who monitors the Dark Web quoted in this story, 12.9GB of data harvested in the ANSA McAL cybersecurity breach by REvil have been released into the wild for public access.
Taylor believes that this is the result of non-payment of the ransom note requested by the cybercrime organisation.
“Clearly not all the data, just the first wave,” he wrote on a Twitter post.
ANSA McAl issued a response to this information on October 27, 2020, stating…
We have been advised that there is certain data purportedly belonging to ANSA McAL which has been made available on the dark web for free and not for sale.
We have taken the prudent decision not to place our people and IT systems at risk by seeking to access the dark web for the purpose of downloading any of these alleged files. As a result, we are unable to verify the authenticity of these claims.
Because the Group’s core systems are largely cloud based and were immediately disabled in accordance with our emergency protocols, the impact of this incident was contained significantly, and our recovery process is largely complete.
Our businesses have and continue to operate in service of our customers and clients.
Original story from October 19, 2020 follows.
In a press release issued on October 17, Rachel Pilgrim, Group Marketing Manager Barbados reported that some of the companies’ IT systems on that island were compromised.
ANSA McAl Trinidad and Tobago declined to answer questions about the nature of the cybersecurity incident or whether any TT companies or services had been affected.
The press release said…
We can confirm that some of our companies’ IT systems in Barbados are down due to a security incident.
As a precautionary measure, some of our services to customers and clients are unavailable.
As we carefully work through the restoration process, we are taking prudent and measured steps to ensure the integrity of our systems. Our teams continue to work on this incident and towards returning services to our clients as our highest priority.
Rest assured we have and will continue to keep our customers informed and appraised on this situation. We take the security of our IT systems extremely seriously and regret any inconvenience.
The company stated that any further information on the matter would be communicated via official press release.
UPDATED: October 20, 2020, with additional information and specifics on the hack.
In a press release dated October 20, 2020, ANSA McAl acknowledged that the “security incident” had impacted the operations of TATIL and TATIL Life, the company’s insurance companies.
The company announced “the support of international resources” engaged in ensuring the integrity of its systems.
The release described the consequences of the attack as a “moderate disruption in service” and continues to serve customers at TATIL’s Head Office and its branch locations.
Cybersecurity and ransomware specialist Eric Taylor @ITSimplifie reports that the cyberterrorist group REvil has taken credit for a ransomware attack on ANSA McAl.
REvil also operates as Sodin and Sodinokibi.
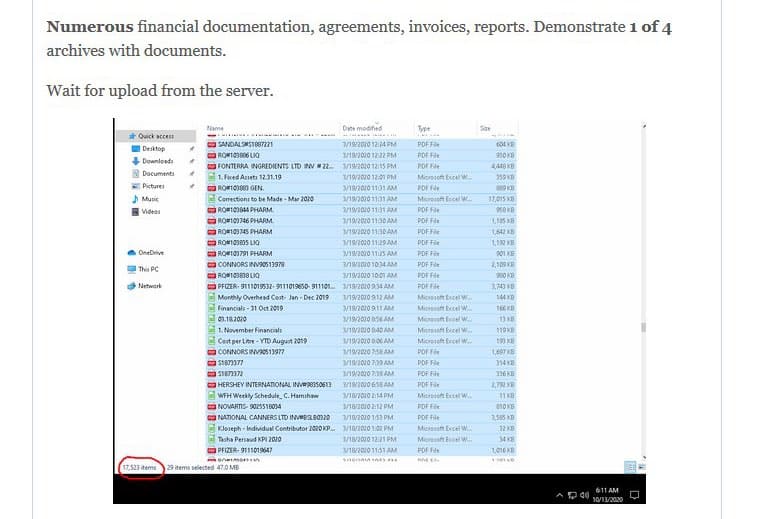
The ransomware group claims to have “numerous financial documentation (sic), agreements, invoices, reports.” A screenshot of the hacked haul reveals a count of 17,000 documents. The group threatens in the post that confirms the hack to release the confidential documents to a public server.
Once the group has the documents in hand, it posts a sample of the stolen documents to an auction page on the Dark Web server Happy Blog and sells the documents to the highest bidder. Payments are made in cryptocurrency.
 REvil has been operating since June 2020. Past auctions have started at US$50,000 in virtual currency.
REvil has been operating since June 2020. Past auctions have started at US$50,000 in virtual currency.
In a typical ransomware attack, the cyberattacker will gain access to a computer system and lock out its legitimate users using sophisticated encryption, demanding a fee to release the data.
Far fewer cyberattacks result in the exfiltration of company data, but those numbers have been increasing.
Ransomware gangs have been feeling a financial pinch since Covid-19 and have been tightening the screws on their victims. Some gangs have charged one fee to release the information to the originating company and another to delete it from their servers.
According to BankInfoSecurity.com, “60% of first-quarter attacks traced to Sodinokibi, Maze and Phobos, by the second quarter, these top three families only accounted for 30% of attacks.”
The average successful extortion payment rose from US$112,000 to nearly $180,000, Ransomware affiliates, who help with the distribution of the attacking malware, can earn as much as $5,000 from a successful attack and extortion.
The NoMoreRansom website is a repository of decryption keys for some known ransomware encryption software, but currently has no keys for the new strains created by REvil/Sodinokibi.
The Trinidad and Tobago Cybersecurity Incident Response Team (TT-CSIRT) has published a notice about ransomware, urging local companies to contact them when incidents occur.
The notice advised, in part…
If you become infected, isolate the affected system(s) immediately by removing the infected system from all networks, and disable all potential networking capabilities. Ensure all shared and networked drives are disconnected whether wired or wireless.
Infected systems will have to be analyzed by your security team or your security provider to determine whether the encrypted data is recoverable.

